Cloud analysis of local evidence sources
One of the main benefits of analysing evidence in AWS is that we can spin up instances with vast amounts of processing power without too much trouble or cost (in the short term). This can greatly decrease processing time of evidence items and is really useful when you need to determine answers quickly.
A few things that may stand in your way:
- ISP Bandwidth limitations for evidence uploads
- Legal or contractual issues around moving evidence into the cloud
- The sheer volume of evidence for upload
Upload of a local .E01
Presumably, you’ve imaged and hashed your evidence, made sure it’s not encrypted with FileVault or BitLocker and you’re ready to dig in. We can now upload some evidence to our AWS storage volume for analysis.
There are many SSH clients out there which you can use for transferring evidence to AWS, PuTTy being the most commonly used. As I’m an unwashed Mac user, my personal favourite is Cyberduck.
Once we have connected through SSH we can upload our evidence and as you can see this 7GB image is going to take around 30 minutes over a business fibre broadband connection.
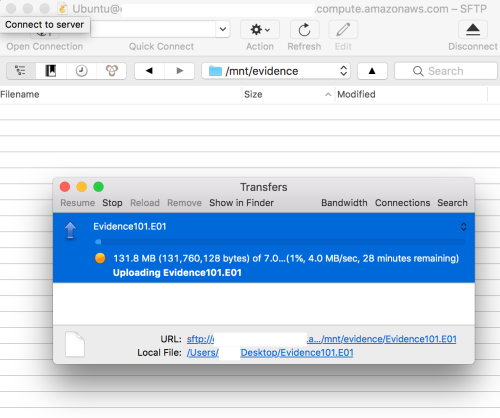
Once our evidence is uploaded we, of course, want to hash it again for integrity checks and for continuity.
ubuntu@ip-17x-x1-x-x9:/mnt/evidence$ md5sum Evidence101.E01
We can now get into the fun stuff. 🙂
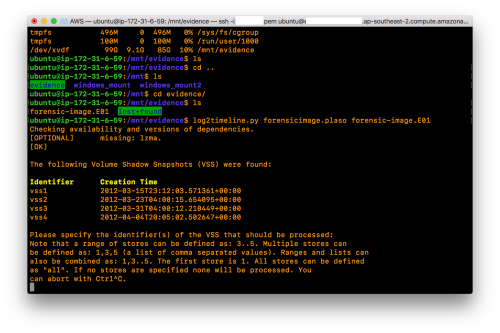
Tools like Log2Timeline will work with as many threads as you can allocate and this is where your more beefy instances with more CPU grunt will really shine.
Looking at the Windows options for online analysis, there is obviously a vast swathe of forensic tools which can be run in Windows too. Although, the issue with some Windows commercial forensic packages is their reliance on hardware dongles. No matter, there’s a solution for that too, which involves setting up a local USB server to share the dongle to a remote host.
Enter VirtualHere.
VirtualHere is also a great way to share dongles across systems in your local network too.
So now we have some processed output, we can either analyse this in place using tools installed in our cloud instance or pull it down using our SSH client to our local system.
Next up, I’ll cover the slightly more complex issue of capturing evidence from an AWS instance.
Reference:
https://www.forensicswiki.org/wiki/Encase_image_file_format
https://bsmuir.kinja.com/building-a-licence-dongle-server-with-a-raspberry-pi-1678930193
